Network and security is a vital discussion point for company leaders thinking about cloud computing. The benefits of using cloud resources are commonly shadowed by thoughts of security risks. These thoughts are reinforced with news of frequent data breaches, which are affecting some of the largest corporations.
So how can you confidently access AIX cloud resources? There are two common ways to remotely access AIX workloads running in the cloud:
- Build a Secure VPN tunnel to the AIX cloud environment. This lets you leverage your existing Internet access gateway and encrypt the communication between the business and the AIX cloud environment. This approach is commonly used to securely connect small remote offices/branches to corporate networks.
- Provision a dedicated/private link. A private link can provide higher performance and reliability, lower latency, and improved security than typical Internet connections. There is also a higher cost and fixed-term contract associated with private links.
Secure VPN Tunnel
For those looking to get started using the AIX cloud, we recommend using an encrypted site-to-site VPN tunnel over an Internet link. This enables the AIX cloud resources to be securely connected to the corporate infrastructure with minimal upfront effort or costs compared to dedicated/private communication lines. Using a secure VPN tunnel, the AIX cloud resources become just another remote office/branch running your AIX test/dev workload.
Look for an AIX cloud provider that offers a managed Internet firewall to establish a secure VPN tunnel and an unmetered network connection with billing based on their 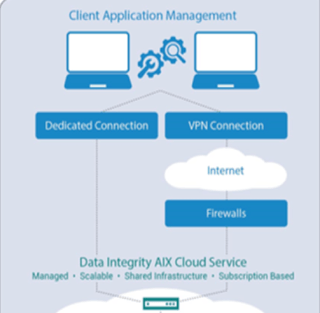 subscribed bandwidth, so there are no surprise networking charges at the end of each billing period.
subscribed bandwidth, so there are no surprise networking charges at the end of each billing period.
Dedicated/Private Link
If you have specific performance or security expectations, you can choose to use a private/dedicated link, such as an extended LAN or MPLS connection, to establish communication between the corporate environment and the AIX cloud environment.
Once you establish the remote connection, you can assign the AIX virtual servers to use IP addresses that align with your corporate addressing schema. This ensures IP reachability throughout the corporate environment and ensures there are no conflicts with overlapping addresses.
We provision the AIX virtual server resources on a dedicated LAN, and continue to provide ongoing systems management for the underlining hardware and operating systems, giving you the freedom to focus on the application workload, rather than worrying about system maintenance and security.
In addition to the security measures taken to protect the environment, you can then integrate your existing corporate tools to enhance the security of your virtual servers. For example, you could use your own single sign-on (SSO) tools, or security monitoring agents, just as you would for your on-premises systems, allowing you to extend security management into the AIX Cloud.
Conclusion
Customers can confidently use AIX cloud resources using industry proven technology to encrypt communications, leverage Data Integrity to manage the maintenance and security of the cloud infrastructure, and bring their own security management suite to provide full visibility into their AIX cloud environment.
All the benefits of cloud computing can be realized with the expectation that the resources are secured as if you were running the workloads in your own data center.


